Trojan horse and malware protection
 Explain A Trojan Horse To A Five-year-old
Explain A Trojan Horse To A Five-year-old  What is a Trojan Horse malware - how to
What is a Trojan Horse malware - how to  Malware, Trojan, Virus, and Worm
Malware, Trojan, Virus, and Worm  What is a Trojan Horse? How it works
What is a Trojan Horse? How it works  How to spot a Trojan horse virus — and
How to spot a Trojan horse virus — and  Trojan Horse—What Is It? Virus or
Trojan Horse—What Is It? Virus or  The-Most-Common-Types-of-Malware-Trojan
The-Most-Common-Types-of-Malware-Trojan  Computer Trojan Horse Malware Or Any
Computer Trojan Horse Malware Or Any  What is Malware? - Definition from
What is Malware? - Definition from  Trojan Horse Malware Computer Virus On
Trojan Horse Malware Computer Virus On  Trojan horse
Trojan horse  Computer Viruses, Worms and Trojans
Computer Viruses, Worms and Trojans  Cyber Attacks: Worms, Trojan Horse
Cyber Attacks: Worms, Trojan Horse  What is a Trojan Horse Virus
What is a Trojan Horse Virus  malware, Trojan, Phishing, and hacking
malware, Trojan, Phishing, and hacking 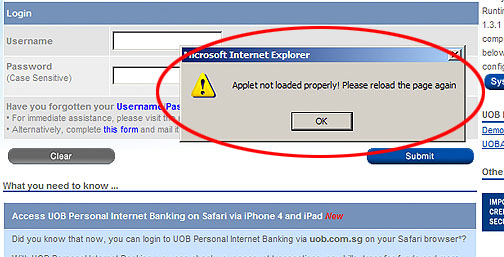 Trojan Horse malware targeting Local Banks
Trojan Horse malware targeting Local Banks  Trojan horse Malware Computer Icons
Trojan horse Malware Computer Icons  Trojan Horse Malware
Trojan Horse Malware  What is a Trojan Horse Virus? | How to
What is a Trojan Horse Virus? | How to  Common Malware Types: Vulnerability
Common Malware Types: Vulnerability  Trojan horse Computer virus Malware
Trojan horse Computer virus Malware  Conficker Computer Virus Malware Trojan
Conficker Computer Virus Malware Trojan  Trojan Horse Examples \u0026 How to Defend
Trojan Horse Examples \u0026 How to Defend  Virus, Trojan, Ransomware, Spyware
Virus, Trojan, Ransomware, Spyware  360 Total Security
360 Total Security  No Trojan Horse Malware Virus Computer
No Trojan Horse Malware Virus Computer  Flashback trojan horse malware pretends
Flashback trojan horse malware pretends  viruses, trojans and malicious software
viruses, trojans and malicious software  Trojan Horse Malware Computer Virus On
Trojan Horse Malware Computer Virus On 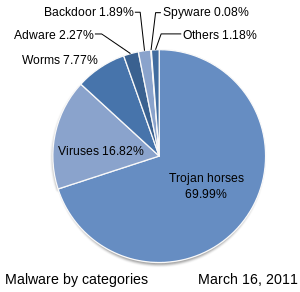 Malware - Wikipedia
Malware - Wikipedia  No Trojan Horse Malware Virus Computer
No Trojan Horse Malware Virus Computer 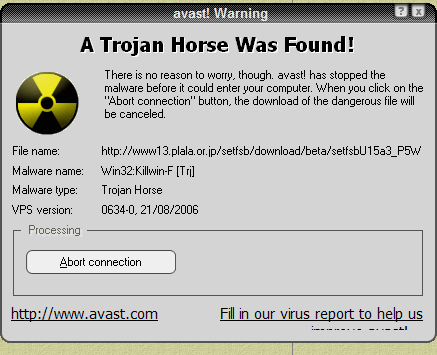 BlackEnergy - the most dangerous virus
BlackEnergy - the most dangerous virus  Trojan Horse, Computer Virus
Trojan Horse, Computer Virus  Trojan Horse Malware Protection Vector
Trojan Horse Malware Protection Vector  Viruses, Worms and Spyware—Yikes! A
Viruses, Worms and Spyware—Yikes! A
Nice Attack: Five People To Appear in Court trojan horse malware Labour Veteran Angela Eagle to Challenge Corbyn for Leadership Post trojan horse malware Brexit: Tusk Tells U.K. It Cannot Have Single Market 'à La Carte' trojan horse malware Taliban and ISIS Both Claim Quetta Hospital Suicide Bombing trojan horse malware
trojan horse malware Gold White Black Red Blue Beige Grey Price Rose Orange Purple Green Yellow Cyan Bordeaux pink Indigo Brown Silver