Trojan Horse | your ict clubs
 What is a Trojan Horse, and how can we
What is a Trojan Horse, and how can we  What Is a Trojan Horse Attack? Plus 3
What Is a Trojan Horse Attack? Plus 3  Trojan Virus | Trojan Virus Definition
Trojan Virus | Trojan Virus Definition  Show Cyber Security Concept
Show Cyber Security Concept  Trojan Horse Laptop Computer Malicious
Trojan Horse Laptop Computer Malicious  What Is a Trojan Horse Attack? Plus 3
What Is a Trojan Horse Attack? Plus 3  Computer virus Malware Trojan horse
Computer virus Malware Trojan horse  Computer Virus Antivirus Software
Computer Virus Antivirus Software  What is Trojan Virus | How to Remove
What is Trojan Virus | How to Remove  Virus, a Trojan, a Worm, and a Rootkit
Virus, a Trojan, a Worm, and a Rootkit  Blog Njrat - Wo - Hacker Transparent PNG
Blog Njrat - Wo - Hacker Transparent PNG  6.1 Trojans introduction – CBTUniversity
6.1 Trojans introduction – CBTUniversity  3 Ways to Get Rid of Trojan Horses
3 Ways to Get Rid of Trojan Horses  Conficker Computer Virus Malware Trojan
Conficker Computer Virus Malware Trojan  Trojan Horse Scanning And Removal
Trojan Horse Scanning And Removal  Antivirus Software, Nexusguard Limited
Antivirus Software, Nexusguard Limited  Computer virus Trojan horse Malware
Computer virus Trojan horse Malware  PC and Devices Against a Trojan Horse Virus
PC and Devices Against a Trojan Horse Virus  Trojan horse
Trojan horse  Malware Computer Virus Malicious
Malware Computer Virus Malicious  Placeholder Trojan: Writing a Malware
Placeholder Trojan: Writing a Malware  How to remove a Trojan, Virus, Worm, or
How to remove a Trojan, Virus, Worm, or  Trojan Horse, Computer Virus
Trojan Horse, Computer Virus  Computer Virus Malware Trojan Horse
Computer Virus Malware Trojan Horse 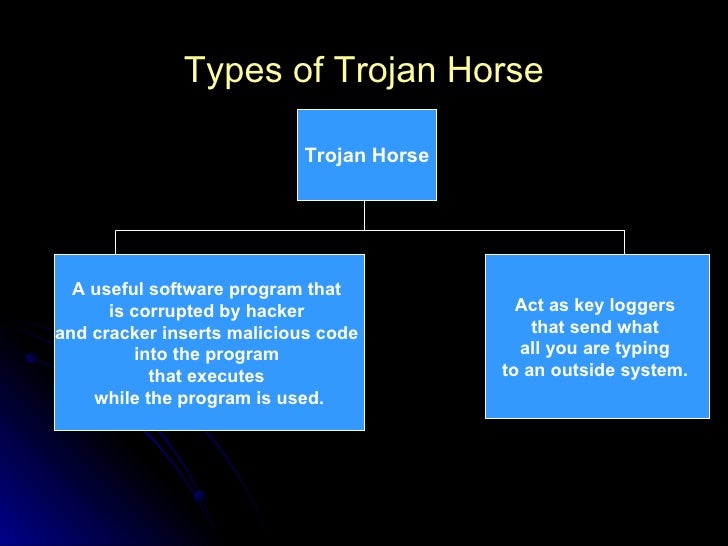 Trojan Horse Virus
Trojan Horse Virus  Trojan horses and its attacks on
Trojan horses and its attacks on  malware, Trojan, Phishing, and hacking
malware, Trojan, Phishing, and hacking  Icon Email, Computer Virus, Icon Design
Icon Email, Computer Virus, Icon Design  Computer Is Infected by a Trojan Horse
Computer Is Infected by a Trojan Horse  Soft-Tech: Trojan horse (computing)
Soft-Tech: Trojan horse (computing)  trojan-horse - SafeBytes Software
trojan-horse - SafeBytes Software 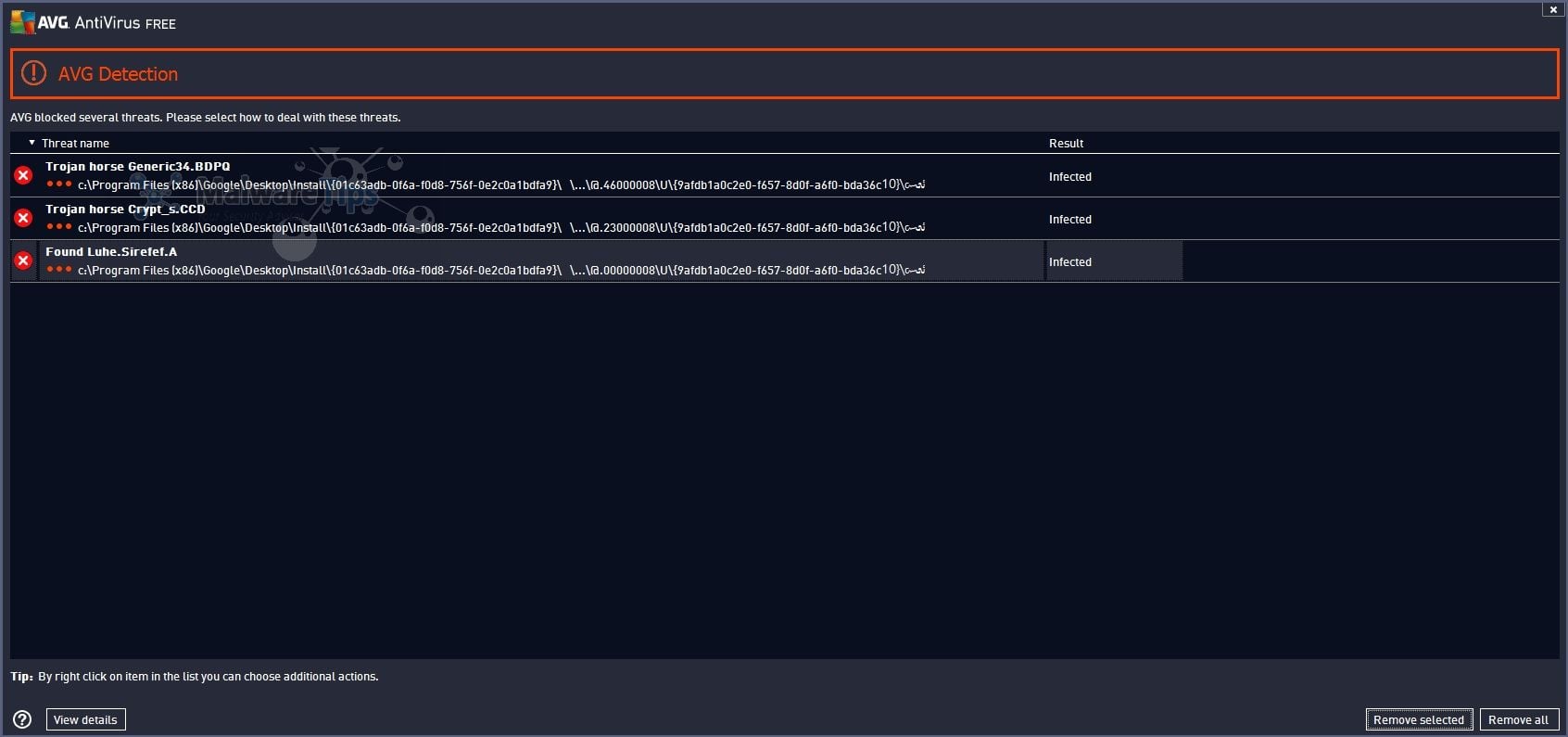 Remove Trojan horse Generic34.BDPQ
Remove Trojan horse Generic34.BDPQ 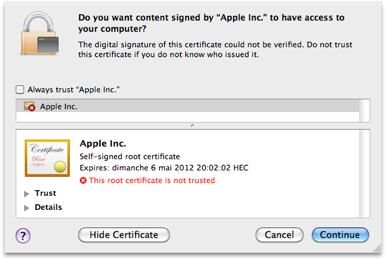 Mac Flashback Trojan horse
Mac Flashback Trojan horse  All About Trojan Horse Viruses | Just
All About Trojan Horse Viruses | Just
Why Putin Is Building a Bridge to Nowhere trojan horse software Rio 2016: Wind Gusts Knock Out Events, Close Shops trojan horse software Chilcot Report: U.S. 'Pushed Britain Into Iraq War,' Says Former Ambassador to U.N. trojan horse software ISIS Leaders Fleeing Mosul Ahead of U.S.-Backed Offensive trojan horse software
trojan horse software Gold White Black Red Blue Beige Grey Price Rose Orange Purple Green Yellow Cyan Bordeaux pink Indigo Brown Silver