
What Is a Trojan Horse Attack? Plus 3
 Trojan Virus | Trojan Virus Definition
Trojan Virus | Trojan Virus Definition  What Is a Trojan Horse Attack? Plus 3
What Is a Trojan Horse Attack? Plus 3  Computer virus Malware Trojan horse
Computer virus Malware Trojan horse  Computer Virus Antivirus Software
Computer Virus Antivirus Software  What is Trojan Virus | How to Remove
What is Trojan Virus | How to Remove  Virus, a Trojan, a Worm, and a Rootkit
Virus, a Trojan, a Worm, and a Rootkit  Remove Trojan Horse | Antivirus program
Remove Trojan Horse | Antivirus program  3 Ways to Get Rid of Trojan Horses
3 Ways to Get Rid of Trojan Horses  Blog Njrat - Wo - Hacker Transparent PNG
Blog Njrat - Wo - Hacker Transparent PNG  3 Ways to Get Rid of Trojan Horses
3 Ways to Get Rid of Trojan Horses  Conficker Computer Virus Malware Trojan
Conficker Computer Virus Malware Trojan  Trojan Horse Scanning And Removal
Trojan Horse Scanning And Removal  Antivirus Software, Nexusguard Limited
Antivirus Software, Nexusguard Limited  Computer virus Trojan horse Malware
Computer virus Trojan horse Malware  PC and Devices Against a Trojan Horse Virus
PC and Devices Against a Trojan Horse Virus  Trojan horse
Trojan horse  Malware Computer Virus Malicious
Malware Computer Virus Malicious  Placeholder Trojan: Writing a Malware
Placeholder Trojan: Writing a Malware  How to remove a Trojan, Virus, Worm, or
How to remove a Trojan, Virus, Worm, or  Trojan Horse, Computer Virus
Trojan Horse, Computer Virus  Computer Virus Malware Trojan Horse
Computer Virus Malware Trojan Horse  Trojan Horse Virus
Trojan Horse Virus  VIRUS WORM TROJAN HORSE ANTI VIRUS
VIRUS WORM TROJAN HORSE ANTI VIRUS  How to Make a Trojan Virus in less than
How to Make a Trojan Virus in less than  Trojan horses and its attacks on
Trojan horses and its attacks on  malware, Trojan, Phishing, and hacking
malware, Trojan, Phishing, and hacking  Icon Email, Computer Virus, Icon Design
Icon Email, Computer Virus, Icon Design  Computer Is Infected by a Trojan Horse
Computer Is Infected by a Trojan Horse  Trojan War Trojan Horse Computer Virus
Trojan War Trojan Horse Computer Virus  Soft-Tech: Trojan horse (computing)
Soft-Tech: Trojan horse (computing)  Computer Virus, Antivirus Software
Computer Virus, Antivirus Software  trojan-horse - SafeBytes Software
trojan-horse - SafeBytes Software 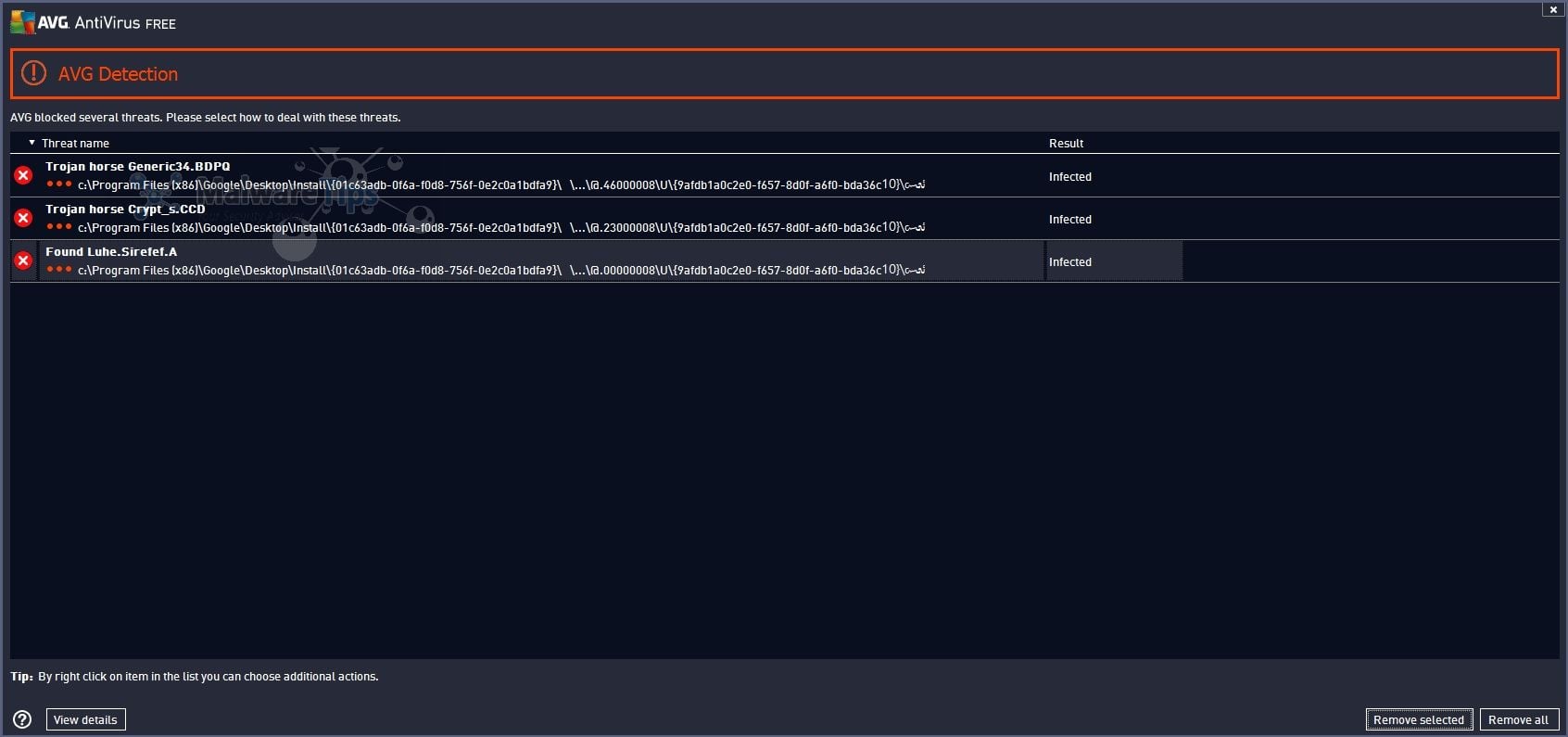 Remove Trojan horse Generic34.BDPQ
Remove Trojan horse Generic34.BDPQ 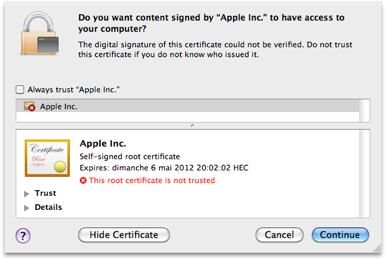 Mac Flashback Trojan horse
Mac Flashback Trojan horse  All About Trojan Horse Viruses | Just
All About Trojan Horse Viruses | Just
ISIS in Afghanistan Claims Capture of U.S. Weapons trojan horse software Uganda’s Top Police Official Summoned Over Torture Allegations trojan horse software At the 2016 Olympics in Rio, Fighting Zika Is Becoming a Blood Sport trojan horse software After Russia's Putin, Erdogan Will Meet With Belarus’s Lukashenko trojan horse software
trojan horse software Gold White Black Red Blue Beige Grey Price Rose Orange Purple Green Yellow Cyan Bordeaux pink Indigo Brown Silver















































![GeTeLe [6 Pack] Cooling Towel trojan horse software](https://m.media-amazon.com/images/I/61jM4BuvS1L._SS250_.jpg)


