Common Trojan Viruses | How to Remove
 Trojan and Virus,Trojan horse,virus,how
Trojan and Virus,Trojan horse,virus,how  SPYWARE AND TROJAN HORSE INFECTIONS
SPYWARE AND TROJAN HORSE INFECTIONS  viruses, trojans and malicious software
viruses, trojans and malicious software  Network Security, Malicious Threats
Network Security, Malicious Threats  9 types of malware and how to recognize
9 types of malware and how to recognize  Infected with Viruses, Malware
Infected with Viruses, Malware  Trojan Horse—What Is It? Virus or
Trojan Horse—What Is It? Virus or  Trojans, Backdoors and Droppers: The
Trojans, Backdoors and Droppers: The  Definition of a Trojan Virus | Computer
Definition of a Trojan Virus | Computer  Study of Most Common Mac OS Threats
Study of Most Common Mac OS Threats  Worms, Trojans \u0026 Bots – Understanding
Worms, Trojans \u0026 Bots – Understanding  Hacking #Linux #KaliLinux #rootsector
Hacking #Linux #KaliLinux #rootsector  Financial Services: Banking Trojans
Financial Services: Banking Trojans  Research interest: Trojans, Backdoors
Research interest: Trojans, Backdoors  should know about computer security threats
should know about computer security threats  Torjan horse virus
Torjan horse virus  Trojan Horse Virus Symptoms | How to
Trojan Horse Virus Symptoms | How to  Cyber Security Attacks – Techlifezine
Cyber Security Attacks – Techlifezine  Malware - Wikipedia
Malware - Wikipedia  Malware, Rootkits, and Trojans
Malware, Rootkits, and Trojans  What is malware? A guide to the 12 most
What is malware? A guide to the 12 most  Torjan horse virus
Torjan horse virus 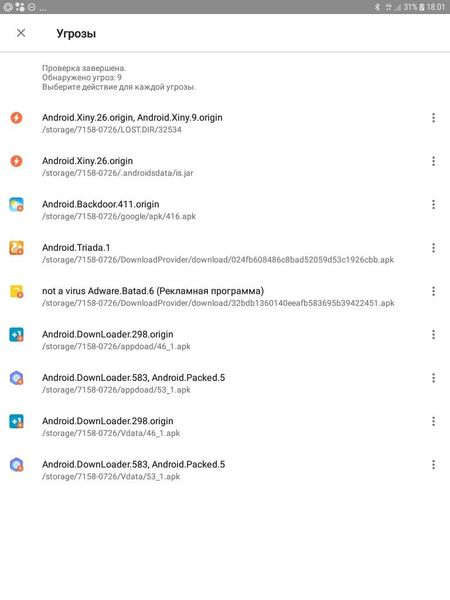 How many Trojans can one smart phone hold?
How many Trojans can one smart phone hold?  8 Common Types of Malware Explained in
8 Common Types of Malware Explained in  PDF) A Cyber Kill Chain Based Analysis
PDF) A Cyber Kill Chain Based Analysis 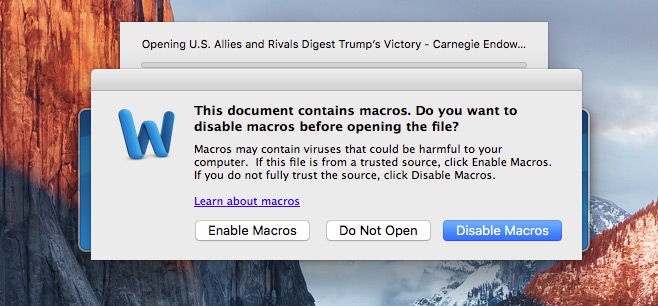 Word file exploit discovered
Word file exploit discovered  Mohamed Sharaf El-Deen
Mohamed Sharaf El-Deen  Common Malware Types: Vulnerability
Common Malware Types: Vulnerability  Virus, a Trojan, a Worm, and a Rootkit
Virus, a Trojan, a Worm, and a Rootkit  IT threat evolution Q3 2019. Statistics
IT threat evolution Q3 2019. Statistics  Different Examples of a Trojan Horse
Different Examples of a Trojan Horse 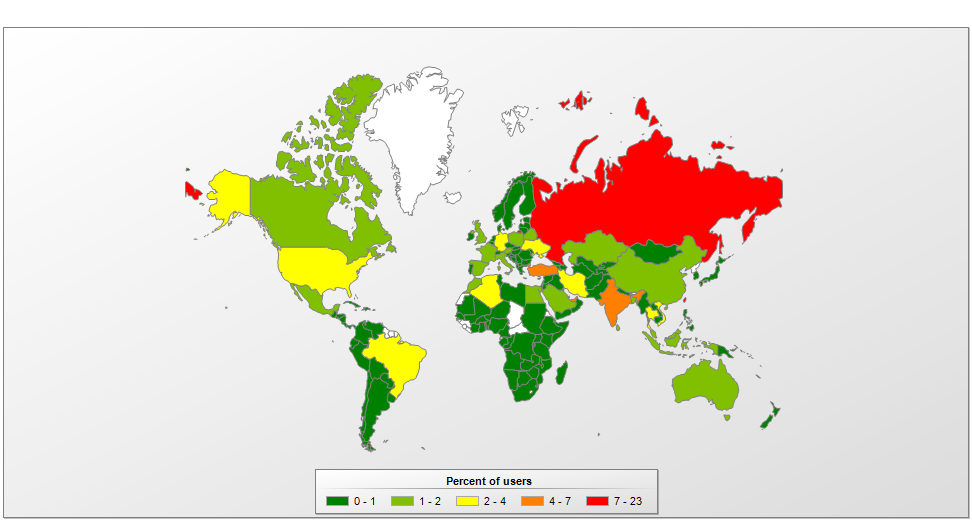 Kaspersky Threats — Neurevt
Kaspersky Threats — Neurevt  Common types of cybersecurity attacks
Common types of cybersecurity attacks
UKIP Leader Nigel Farage: ‘The Euroskeptic Genie is Out of the Bottle’ common trojans How the Media Fell for Putin’s Stealth Invasion common trojans Uganda’s Top Police Official Summoned Over Torture Allegations common trojans Brexit: Nicola Sturgeon to Start ‘Immediate Discussions’ With EU Over Scotland’s Status common trojans
common trojans Gold White Black Red Blue Beige Grey Price Rose Orange Purple Green Yellow Cyan Bordeaux pink Indigo Brown Silver










































:max_bytes(150000):strip_icc()/GettyImages-147215503-7e202a7619544efb9e6ed1bb41c00787.jpg)










-500x500.jpg)