Real Trojan Horses — A Case for
 Trojan Horse Computer Virus
Trojan Horse Computer Virus  TROJAN HORSE SECURITY - Reviews | Facebook
TROJAN HORSE SECURITY - Reviews | Facebook  What Do Trojan Viruses Do? | How To
What Do Trojan Viruses Do? | How To  Trojan Horse Security hacker Computer
Trojan Horse Security hacker Computer  Trojan horse' stalks security
Trojan horse' stalks security  Trojan Virus | Trojan Virus Definition
Trojan Virus | Trojan Virus Definition  What is a Trojan virus? How this tricky
What is a Trojan virus? How this tricky  Trojan Horse Icon In Badge Style. One
Trojan Horse Icon In Badge Style. One  Icons. Premium Quality Graphic Design
Icons. Premium Quality Graphic Design  Types of Trojan Attacks 2015. Network
Types of Trojan Attacks 2015. Network  Trojan Horse Virus Mal-ware Cyber
Trojan Horse Virus Mal-ware Cyber  Home Router…, or Trojan Horse
Home Router…, or Trojan Horse  Trojan Horse Computer Security Program
Trojan Horse Computer Security Program  horse, security, trojan, virus icon
horse, security, trojan, virus icon  Horse, security, trojan, virus icon
Horse, security, trojan, virus icon  Bring your own device, Byod, Trojan horse
Bring your own device, Byod, Trojan horse  What is a Trojan Horse Virus? | How to
What is a Trojan Horse Virus? | How to  Computer Virus Trojan Horse Malware
Computer Virus Trojan Horse Malware  INFORMATION SECURITY DISCUSSION © 2015
INFORMATION SECURITY DISCUSSION © 2015  The story of the Trojan Horse from an
The story of the Trojan Horse from an  What is a Trojan? | IT PRO
What is a Trojan? | IT PRO  Comodo Antivirus | Computer security
Comodo Antivirus | Computer security  Trojan Horse Security Risk Stock Vector
Trojan Horse Security Risk Stock Vector  BBC Radio 5 Live Stephen Nolan Show
BBC Radio 5 Live Stephen Nolan Show  SPYWARE AND TROJAN HORSE INFECTIONS
SPYWARE AND TROJAN HORSE INFECTIONS  TROJAN HORSE SECURITY- | Information
TROJAN HORSE SECURITY- | Information  TROJANHORSE SECURITY (@TROJANHORSESECU
TROJANHORSE SECURITY (@TROJANHORSESECU  Trojan Horse Malware Vector \u0026 Photo
Trojan Horse Malware Vector \u0026 Photo  Malware, Spyware, Trojan Horse
Malware, Spyware, Trojan Horse 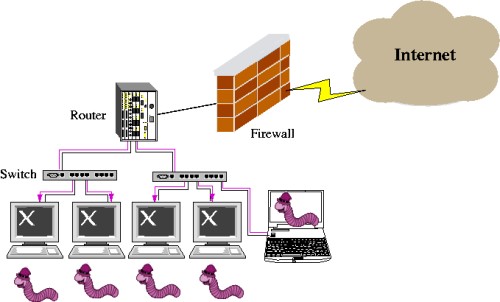 CCNA Security: Worm, Virus and Trojan
CCNA Security: Worm, Virus and Trojan  the original trojan horse
the original trojan horse  Antivirus Software, Nexusguard Limited
Antivirus Software, Nexusguard Limited  Computer Security Malware Database
Computer Security Malware Database
Isabel Oakeshott: History Will Judge David Cameron Harshly For Brexit Campaign trojan horse security Europeans Fear Refugees Will Bring Terrorism, Take Jobs: Study trojan horse security Excavate History WWII-Era Tunnel Unearths Story of Lithuania's Jews trojan horse security Larry the Cat Remains in Downing Street, Despite Cameron's Departure trojan horse security
trojan horse security Gold White Black Red Blue Beige Grey Price Rose Orange Purple Green Yellow Cyan Bordeaux pink Indigo Brown Silver