TROJAN HORSE SECURITY - Reviews | Facebook
 Trojan Horse Computer Virus
Trojan Horse Computer Virus  What Do Trojan Viruses Do? | How To
What Do Trojan Viruses Do? | How To  Trojan Horse Security hacker Computer
Trojan Horse Security hacker Computer  Trojan horse' stalks security
Trojan horse' stalks security  Trojan Virus | Trojan Virus Definition
Trojan Virus | Trojan Virus Definition  What Exactly Does A Trojan Horse Do?
What Exactly Does A Trojan Horse Do?  What is a Trojan virus? How this tricky
What is a Trojan virus? How this tricky  Trojan Horse Icon In Badge Style. One
Trojan Horse Icon In Badge Style. One  Icons. Premium Quality Graphic Design
Icons. Premium Quality Graphic Design  Types of Trojan Attacks 2015. Network
Types of Trojan Attacks 2015. Network  Trojan Horse Virus Mal-ware Cyber
Trojan Horse Virus Mal-ware Cyber  Home Router…, or Trojan Horse
Home Router…, or Trojan Horse  Trojan Horse Computer Security Program
Trojan Horse Computer Security Program  Horse, security, trojan, virus icon
Horse, security, trojan, virus icon  Bring your own device, Byod, Trojan horse
Bring your own device, Byod, Trojan horse  Computer Virus Trojan Horse Malware
Computer Virus Trojan Horse Malware  INFORMATION SECURITY DISCUSSION © 2015
INFORMATION SECURITY DISCUSSION © 2015  The story of the Trojan Horse from an
The story of the Trojan Horse from an  Comodo Antivirus | Computer security
Comodo Antivirus | Computer security  Trojan Horse Security Risk Stock Vector
Trojan Horse Security Risk Stock Vector  BBC Radio 5 Live Stephen Nolan Show
BBC Radio 5 Live Stephen Nolan Show  Trojan Horse Computer Security
Trojan Horse Computer Security  TROJAN HORSE SECURITY - About | Facebook
TROJAN HORSE SECURITY - About | Facebook  SPYWARE AND TROJAN HORSE INFECTIONS
SPYWARE AND TROJAN HORSE INFECTIONS  Computer virus Malware Trojan horse
Computer virus Malware Trojan horse  TROJAN HORSE SECURITY- | Information
TROJAN HORSE SECURITY- | Information  Trojan Horse Examples \u0026 How to Defend
Trojan Horse Examples \u0026 How to Defend  TROJANHORSE SECURITY (@TROJANHORSESECU
TROJANHORSE SECURITY (@TROJANHORSESECU  Malware, Spyware, Trojan Horse
Malware, Spyware, Trojan Horse  Trojan Horse Security in Miami Newsday
Trojan Horse Security in Miami Newsday 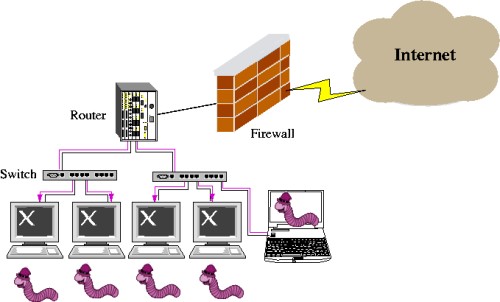 CCNA Security: Worm, Virus and Trojan
CCNA Security: Worm, Virus and Trojan  the original trojan horse
the original trojan horse  Computer Security Malware Database
Computer Security Malware Database
Clement Freud Lunged At Me,' Says Fourth Woman trojan horse security Iraq War Was Illegal, Ex-deputy PM Prescott Says trojan horse security France to Redeploy Aircraft Carrier For Fight Against ISIS: Hollande trojan horse security Why New Israeli Settlements Set Back the Day of Peace trojan horse security
trojan horse security Gold White Black Red Blue Beige Grey Price Rose Orange Purple Green Yellow Cyan Bordeaux pink Indigo Brown Silver