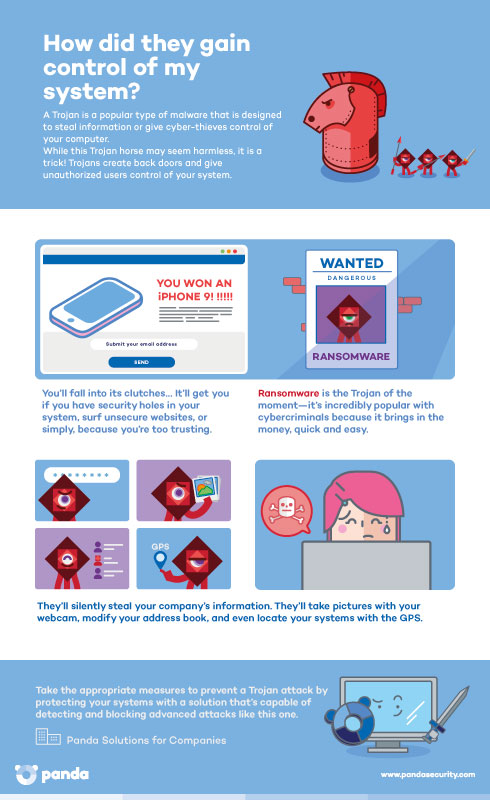
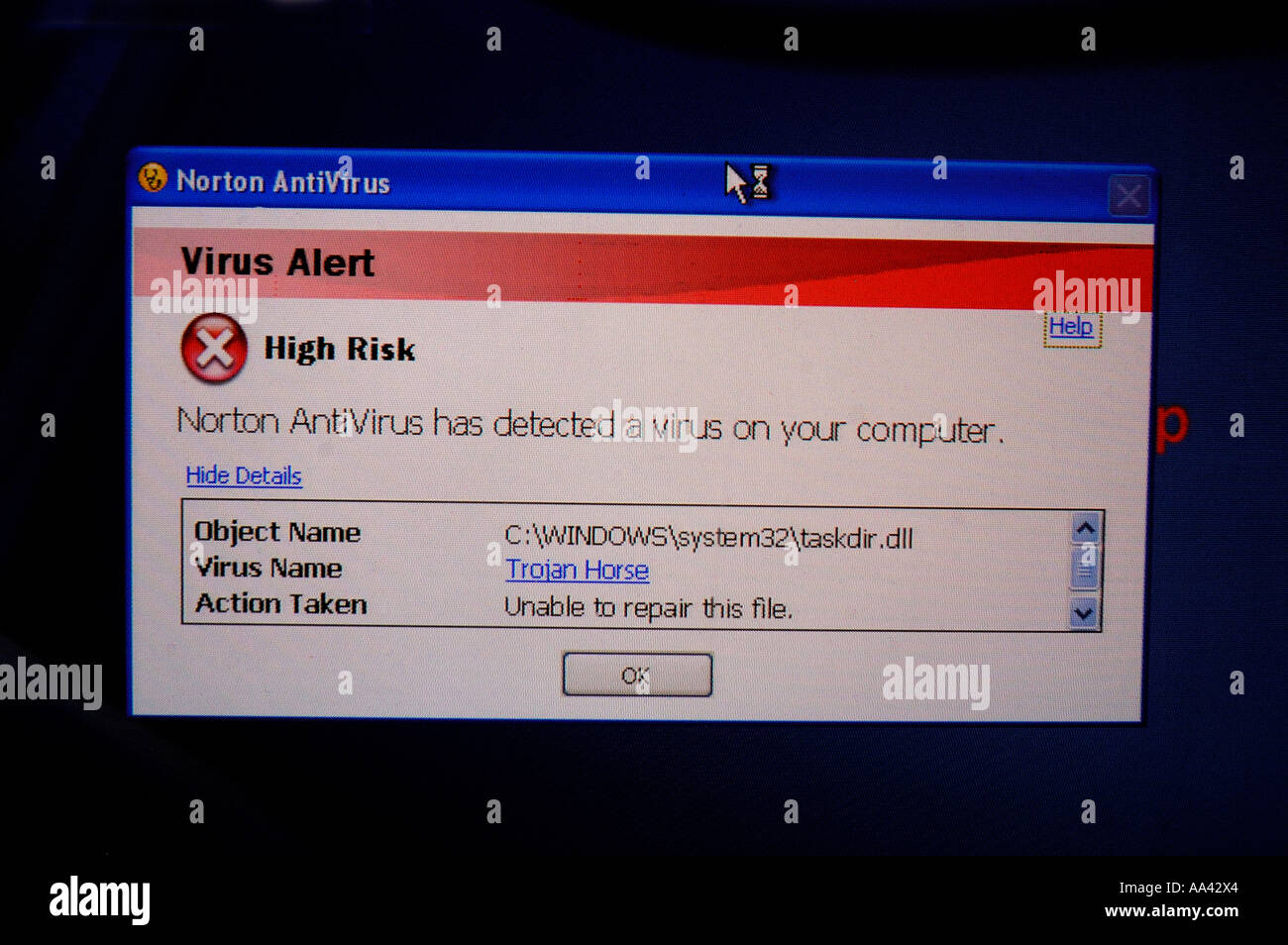
Trojan Attacks | How Does Trojan Horse
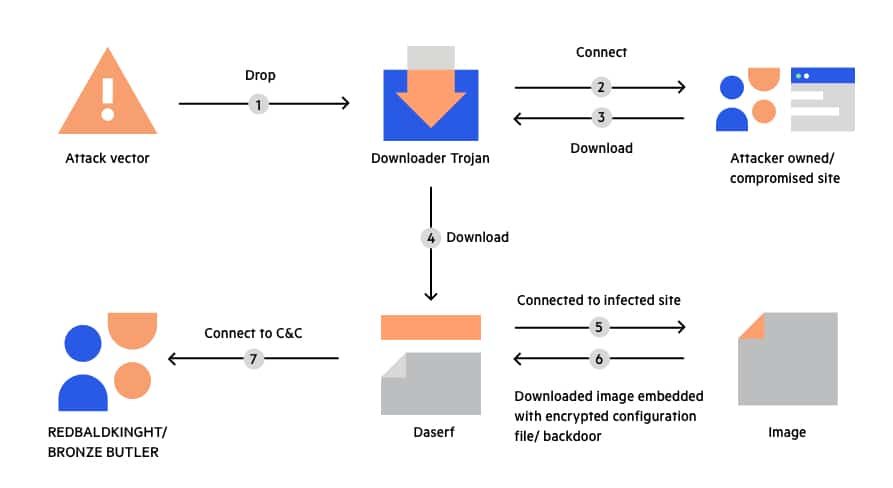
 CCNA Security: Worm, Virus and Trojan
CCNA Security: Worm, Virus and Trojan  What is a Trojan Horse Virus? | How to
What is a Trojan Horse Virus? | How to  Trojan Horse Virus Infect Smartphone
Trojan Horse Virus Infect Smartphone  What Is a Trojan Horse Attack? Plus 3
What Is a Trojan Horse Attack? Plus 3  What is a Trojan Horse Virus
What is a Trojan Horse Virus  What Is Trojan Virus? | How To Protect
What Is Trojan Virus? | How To Protect  Trojan Horse Virus Mal-ware Cyber
Trojan Horse Virus Mal-ware Cyber  What is a Trojan Horse malware - how to
What is a Trojan Horse malware - how to  Distributed Denial of Service Attacks
Distributed Denial of Service Attacks  PC and Devices Against a Trojan Horse Virus
PC and Devices Against a Trojan Horse Virus  Trojan Horse Virus Attacks
Trojan Horse Virus Attacks  Trojan Virus High Resolution Stock
Trojan Virus High Resolution Stock 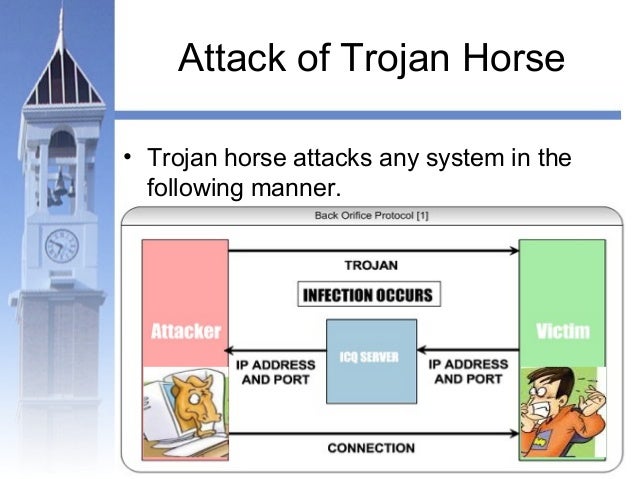 Malicious
Malicious 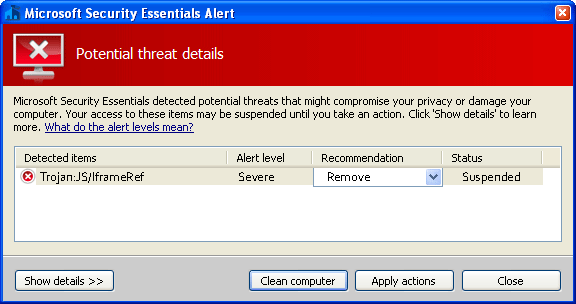 Types of Trojan Attacks 2015. Network
Types of Trojan Attacks 2015. Network  What is a Trojan virus? How this tricky
What is a Trojan virus? How this tricky  virus salami attack and trojan horse
virus salami attack and trojan horse 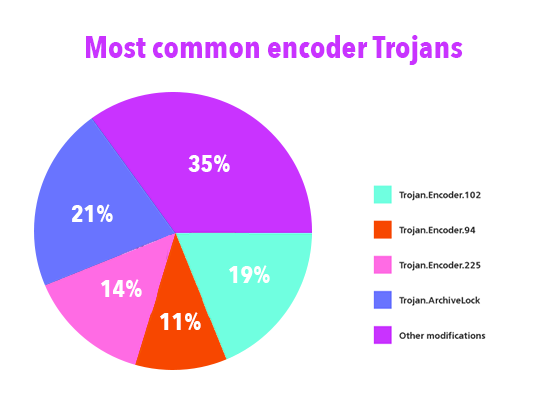 Common Trojan Viruses | How to Remove
Common Trojan Viruses | How to Remove  What is a Trojan Horse malware - how to
What is a Trojan Horse malware - how to  How to spot a Trojan horse virus — and
How to spot a Trojan horse virus — and  How Trojan Horses Work | HowStuffWorks
How Trojan Horses Work | HowStuffWorks  CCNA Security: Worm, Virus and Trojan
CCNA Security: Worm, Virus and Trojan  viruses, trojans and malicious software
viruses, trojans and malicious software  Trojan Horse Malware Effects On
Trojan Horse Malware Effects On  The Differences Between a Virus, Trojan
The Differences Between a Virus, Trojan  Computer Viruses, Worms and Trojans
Computer Viruses, Worms and Trojans  Ways To Prevent Trojan Horse Attacks
Ways To Prevent Trojan Horse Attacks  Trojan Virus | Terra Preta
Trojan Virus | Terra Preta 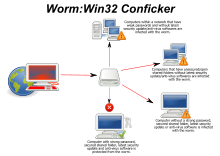 Computer worm - Wikipedia
Computer worm - Wikipedia  Cyber Attacks: Worms, Trojan Horse
Cyber Attacks: Worms, Trojan Horse  Computer Virus Spyware Trojan Horse
Computer Virus Spyware Trojan Horse  Computer Virus Trojan Malware Attack
Computer Virus Trojan Malware Attack  Virus,Worm,Trojan,Backdoor \u0026 Antivirus
Virus,Worm,Trojan,Backdoor \u0026 Antivirus  Computer Trojan Horse Virus Information
Computer Trojan Horse Virus Information
Watch: Queen Jokes About Her Health With Martin McGuinness trojan virus attack Britain Gets First Newspaper For Pro-Europeans trojan virus attack Brexit: Leave Voters Regretful, Wish They'd Voted Remain trojan virus attack Nice Attack: Five People To Appear in Court trojan virus attack
trojan virus attack Gold White Black Red Blue Beige Grey Price Rose Orange Purple Green Yellow Cyan Bordeaux pink Indigo Brown Silver