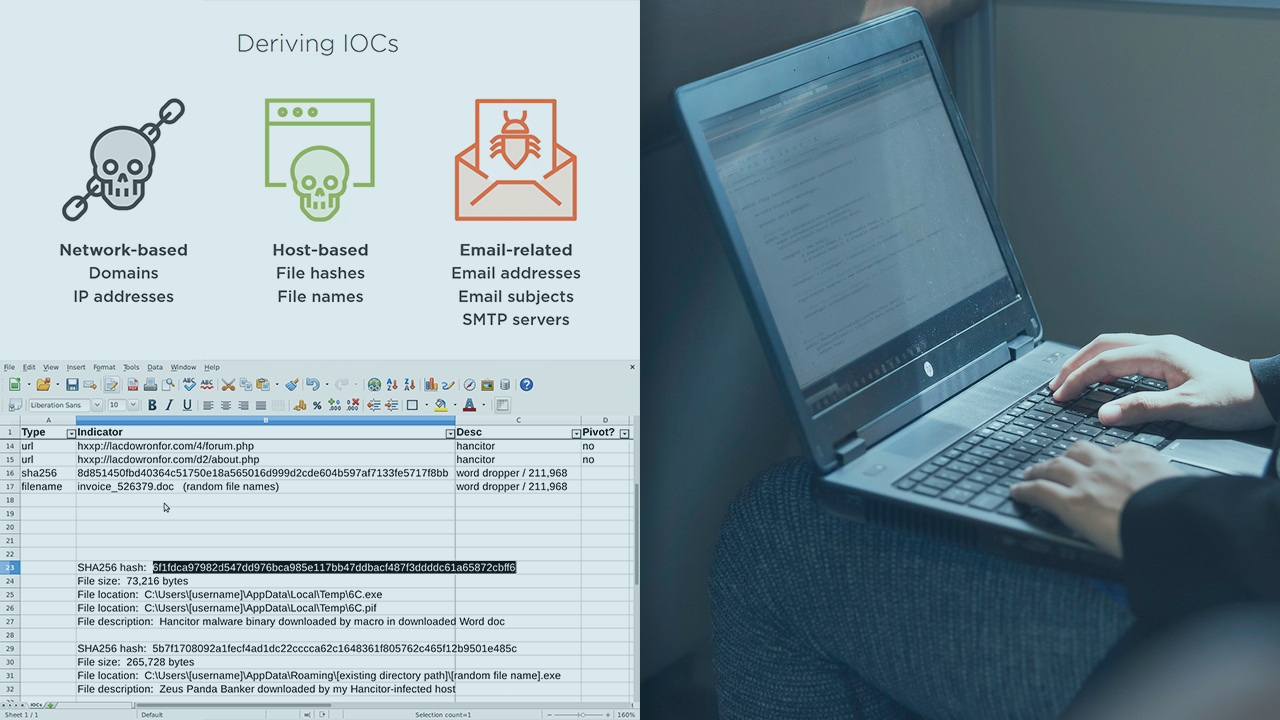
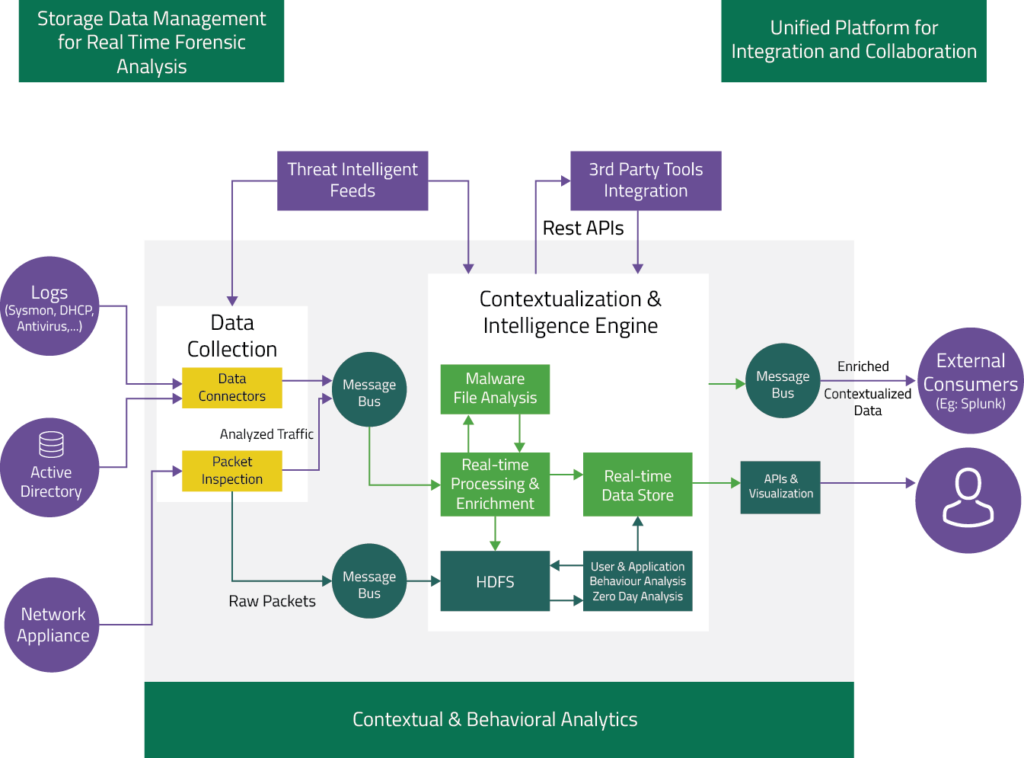
Customer Reviews:
| Full Name: | |
| Title: | |
| Description: | |
| Rating Value: | |
| Time: | 2025-08-09 21:15:57 |
Customers who viewed this item also viewed: